NVIDIA recently announced its latest graphics cards including the NVIDIA 4090. While creators rejoice, there is the longstanding question about how long will it take to crack your password.
The question usually generates a lot of news and I thought it was worth getting into.
First, let’s define our assumptions.
The passwords we are after are the ones where we know the hash. A hash is a mathematical representation of the password using what is called a one-way function. This is a little beyond the scope of this article, but there is a lot out there on how hash algorithms are used. For our purposes, I’ve listed several popular ones in the data. It is important because different hashes are more difficult to calculate or have a higher level of complexity and therefore take longer to brute force crack.
Second, for our benchmark we are using the results of Chick3nman. Their Git repository lists several different hardware benchmarks over time and is a good resource to review. For this benchmark, they have optimized the use of HashCat. Lastly to this point, we are assuming the use of 8 NVIDIA 4090 graphic cards.
Lastly, and this is a bit more controversial, we are assuming passwords include upper case ASCII, lower case ASCII, numbers and special characters for a total of 95 different possible symbols. There is a great mathematical conversation on what the reduced space is for this complexity on StackExchange, but I find the math less than helpful because it is theoretical in nature when applied to our brute force method. What will probably come from this line of thinking is a reduced problem space as people consider ways to reduce the number of ‘unlikely’ combinations. Oh those wiley mathematicians.
So first is the obvious.
Assuming the symbol space, how many possible passwords are there given the length.
| Length | Combinations |
| 1 | 95 |
| 2 | 9,025 |
| 3 | 857,375 |
| 4 | 81,450,625 |
| 5 | 7,737,809,375 |
| 6 | 735,091,890,625 |
| 7 | 69,833,729,609,375 |
| 8 | 6,634,204,312,890,620 |
| 9 | 630,249,409,724,609,000 |
| 10 | 59,873,693,923,837,900,000 |
| 11 | 5,688,000,922,764,600,000,000 |
| 12 | 540,360,087,662,637,000,000,000 |
| 13 | 51,334,208,327,950,500,000,000,000 |
| 14 | 4,876,749,791,155,300,000,000,000,000 |
| 15 | 463,291,230,159,753,000,000,000,000,000 |
| 16 | 44,012,666,865,176,600,000,000,000,000,000 |
| 17 | 4,181,203,352,191,770,000,000,000,000,000,000 |
| 18 | 397,214,318,458,219,000,000,000,000,000,000,000 |
| 19 | 37,735,360,253,530,800,000,000,000,000,000,000,000 |
| 20 | 3,584,859,224,085,420,000,000,000,000,000,000,000,000 |
For our purposes, I’ll only focus on the 7-10 symbol range to keep things simple, but the math is here to support fairly straight forward calculations if you’re interested.
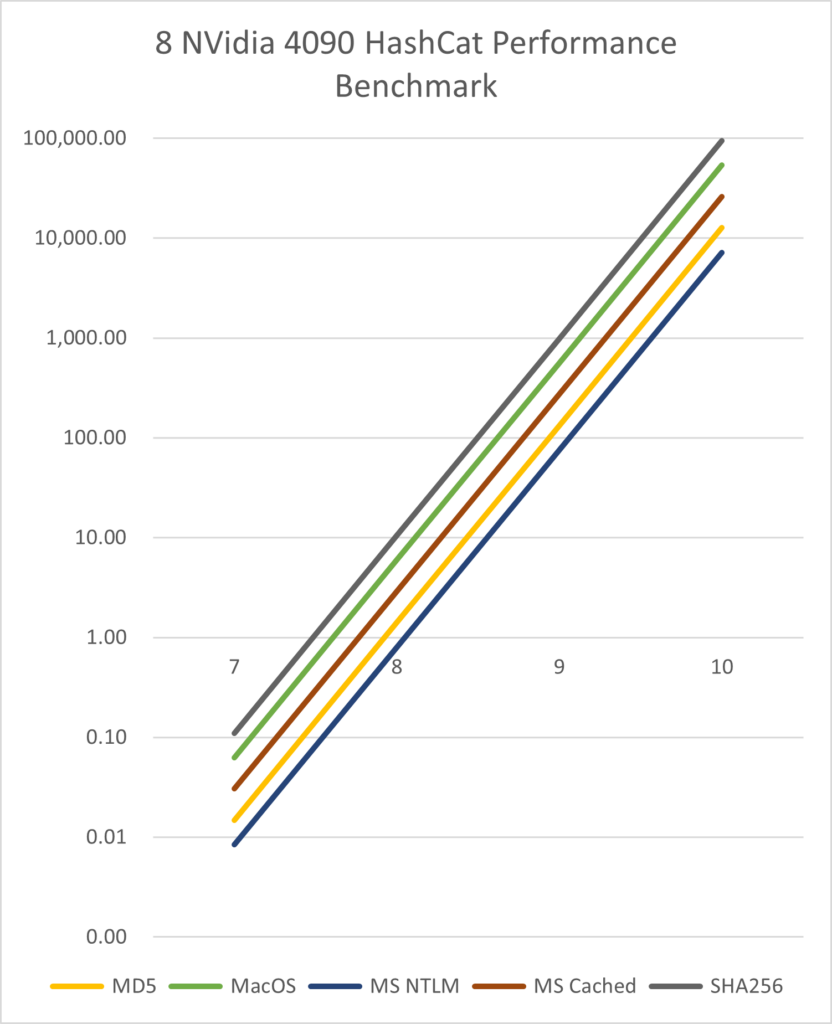
Using our test rig of 8 NVIDIA 4090s and HashCat, how long would it take to break a password using different popular hashing algorithms?
These times are listed in minutes.
| Length | MD4 | MD5 | MD5 + Salt | MacOS | MS NTLM | MS Cached | SHA256 | SHA256 + salt |
| 7 | 0.01 | 0.01 | 0.01 | 0.06 | 0.01 | 0.03 | 0.11 | 0.11 |
| 8 | 0.79 | 1.40 | 1.40 | 5.96 | 0.80 | 2.90 | 10.48 | 10.49 |
| 9 | 75.36 | 133.36 | 133.44 | 566.36 | 75.85 | 275.63 | 995.82 | 996.51 |
| 10 | 7,158.91 | 12,668.79 | 12,676.51 | 53,804.67 | 7,206.06 | 26,185.27 | 94,602.98 | 94,668.46 |
It’s important to keep in mind that this is the worst possible case where Brute Force cracking is necessary. Most passwords can be looked up in a dictionary or rainbow table much, much quicker. I wouldn’t try to state a number here, but any security testing would start there long before going to a rig like this out of efficiency.
So what lessons do we take from this and how should we council our clients?
Before we get into the takeaways, let me just point out that there isn’t a meaningful difference between the hashing methods, meaning that each hash algorithm has a different complexity level, but they are all weak in the same way. The question is how cheaply can this weakness be attacked?
- Pass Phrases not Passwords. Give up the strange combination of letters and symbols with no meanings. Use a pass phrase that is meaningful to you but hard to guess. You’ll still need some unexpected UPPER/lower case letters, numbers and symbols, but a good pass phrase is easier to remember than an obscure password. The Australian Government has a pretty easy reminder of this on their Cyber Security Centre web page. I recommend a pass phrase of 12+ characters with UPPER/lower case, symbols and numbers.
It’s important to remember that passphrases must contain this complexity. As an example of this, it is assumed that most American’s have a vocabulary of about 42,000 words as an adult. That seems pretty optimistic as to how many of those words would be used in a pass phrase, but assume that this is true and they are equally likely to use any of those words, and that they’ve included no other symbol types. It would take about 8 minutes to crack a three word pass phrase by itself. So if you just move to three lowercase words with no other complexity, you’ve actually reduced the time needed to break your password by using either a dictionary or pass phrase attack. - Use different pass phrases for different sites. Just don’t reuse pass phrases but worry less about changing your pass phrase unless you think it may have been stolen. I cannot stress enough that the use of a password manager, for most people, is better than not having one. There are reasons for caution here and most password managers will caution you on how to securely implement them. Follow this advise.
- If it’s important, it should require multi-factor authentication. This can be an authentication application on your phone, but better if its a FIDO2 token. There is a lot of information out there on this that is outside the scope of this article, but check out YubiKey if you’re new to this idea. Remember that SMS text messages are highly insecure. They are HIGHLY insecure, but better than nothing. If your provider is suggesting this method, question them on as to if better options are available.
- If for some reason you didn’t follow the prior advise and you still want to use a password, I recommend nothing less than 12 characters at this point. Remember, its not if someone can break your password, its how much time and effort do they want to put into it.
Lastly, it’s important to remember that there are rational actors out there who attack the weakest element in your security system, you. Most security breaches occur because we are imperfect beings, seek simplicity and tend to be slow to recognize threats in our environment, especially cybersecurity threats.
While it’s fun to look at how the landscape has changed from a technological front, for the majority of people out there, their lack of good security hygiene will be the cause of their own losses.
Stay vigilant my friends. Be aware of your surroundings and question what you think you know.
About the Author
Bill Weber is a Virtual CISO and Entrepreneur located in the United States. He works with clients wanting to better understand risk and create meaningful advantages for their organizations by tackling them creating real long term stability.
You can find his company at cyberfoundry.io.
Comment on LinkedIn
Credit for the cover art to DALL-E.